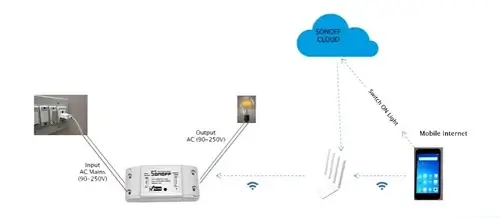
Introduction
The Internet of Things (IoT) is transforming industries and our daily lives by connecting devices in unprecedented ways. However, with great connectivity comes significant security challenges. As IoT networks become more pervasive, they are increasingly targeted by cyber threats. This comprehensive guide explores how to secure your IoT network from potential cyber threats, providing insights from basic security measures to advanced strategies.
Understanding IoT Security
What is IoT Security?
IoT security involves protecting connected devices and networks in the Internet of Things. It encompasses strategies, technologies, and processes designed to safeguard devices and data from unauthorized access and attacks.
Why is IoT Security Important?
- Vulnerability of Devices: Many IoT devices have limited security features, making them vulnerable.
- Data Privacy: IoT devices collect vast amounts of data, which can be sensitive.
- Network Integrity: A breach can compromise the entire network's integrity.
Key Components of IoT Security
Device Authentication and Authorization
Ensuring that only authorized devices can connect to the network is crucial. Implement multi-factor authentication and unique credentials for each device.
Data Encryption
Encrypt data both in transit and at rest to protect it from interception and unauthorized access.
Network Security
Use firewalls, intrusion detection systems, and secure communication protocols like TLS/SSL to safeguard the network.
Common IoT Security Threats
Botnets
Attackers can hijack IoT devices to create botnets for launching Distributed Denial-of-Service (DDoS) attacks.
Data Breaches
Unauthorized access to data can lead to privacy violations and financial losses.
Firmware Vulnerabilities
Poorly secured firmware can be exploited to gain control of a device.
Steps to Secure Your IoT Network
1. Conduct a Security Audit
- Identify all devices connected to your network.
- Assess each device's security settings and vulnerabilities.
2. Implement Strong Password Policies
- Use complex passwords and change them regularly.
- Avoid using default passwords provided by manufacturers.
3. Regular Software and Firmware Updates
- Keep all devices updated with the latest security patches.
4. Segment Your Network
- Create separate networks for IoT devices to limit exposure.
Real-World Examples and Case Studies
An example of an IoT security breach occurred with the Mirai Botnet attack in 2016, where millions of IoT devices were compromised to execute DDoS attacks on major websites.
Future Outlook and Industry Trends
The future of IoT security involves integrating AI for threat detection, enhancing device-level security, and developing industry-wide standards for device manufacturers.
Common Mistakes to Avoid
- Ignoring Device Security: Always prioritize securing each device before deployment.
- Overlooking Network Segmentation: Avoid connecting all devices to a single network without segmentation.
Conclusion and Next Steps
Securing your IoT network is critical in today's digital landscape. By understanding common threats and implementing robust security measures, you can protect your network from potential breaches. Stay informed about new vulnerabilities and continuously update your security practices to ensure comprehensive protection.